Note: This tutorial was created by xiaobaiyey and written in chinese. This tutorial is poorly translated from Google Translation but i have fixed some grammar to make it easier to understand.
reviously I read an article by hook decrypting the encrypted dll Unity3D, recently new to dynamic, so they can try the next through IDA, the same as the shelling, dump the decrypted dll file, try the next, it really can, in here to share under
Requirements:
Tools: IDA6.6. DOWNLOAD LINK
Game: Monthly Dragon knife (just find a game)
Enable USB-debugging in Developer Options
Open lib in IDA:
Unzip lib folder from the APK, drag the file libmono.so to IDA
Several functions mainly in the upper and lower breakpoint (refer mono source )
Code (Text):
mono_image_open_from_data_full
mono_image_open_from_data
mono_image_open_from_data_with_name
In a decryption process can about these function
View the final in front of a function call or mono_image_open_from_data_with_name,
Enable Developer Options:
If Developer Option does not show in settings, follow the steps below.
1. Open Settings > About
2. Then tap “Build number” seven times to enable Developer options....
3. Go back to Settings menu and now you'll be able to see “Developer options” there.
4. Tap it and turn on USB Debugging
Dynamic debugging:
If the app has anti-debugging, you need to skip meals to debug, the following brief dynamic debugging Preparations (there are many online tutorials dynamic debugging)
Get android_server file from IDA PRO 6.6\ida66\dbgsrv or download the file HERE!
Push android_server file to the phone
1:
2:
3:
4:
5:
Port Forwarding:
Debug startup app:
Check the app's PID:
1.
2.
Record the PID and Forwarding (pid can be seen in the ida)
Setting ida (the main settings hostname: 127.0.0.1) and open the attach process (wait for the program to automatically break live, live off later)
Run app (in the f9 at ifa)
This time, open CMD.exe on Windows and run jdb debugger (Java debugger):
This time can be debugged
Run app will break on the linker
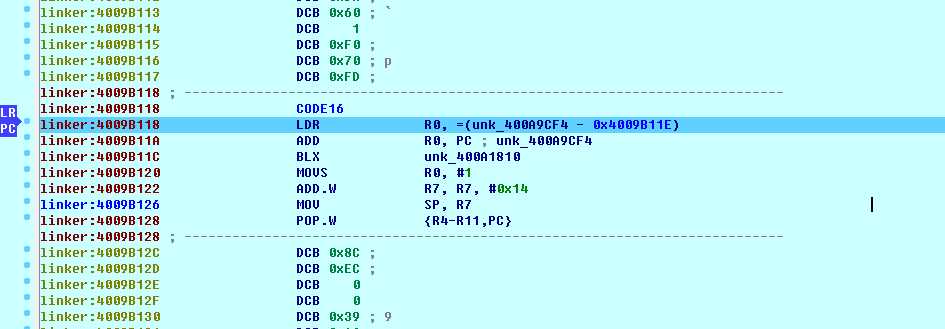
Then if the app is no anti-molestation: running directly f9
This window appears: same point
Wait a moment, will end on Linker , directly connected to f9 op row
If this window appears, select "yes (pass to app)" without waiting
Many may appear behind all this window select yes and then run f9
Finally broken in the mono_image_open_from_data_with_name, method
Loading is not the first time we want to skip dll
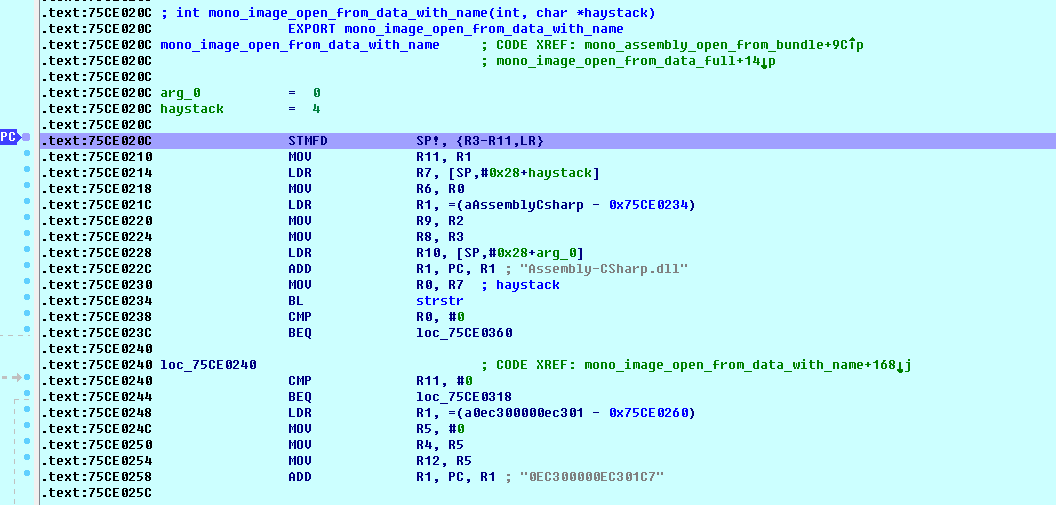
If you can not read f5 look at the source code, source code demonstrate this direct f5, where he rewrote momo source
Several key parameters
This time following the R1 register to see the encrypted DLL file address, indicating the DLL has not yet begun to decrypt, decryption may later. And laid down the road to change a single note of each register after a simple loop
The dll decrypted
This time it decrypted DLL in memory,
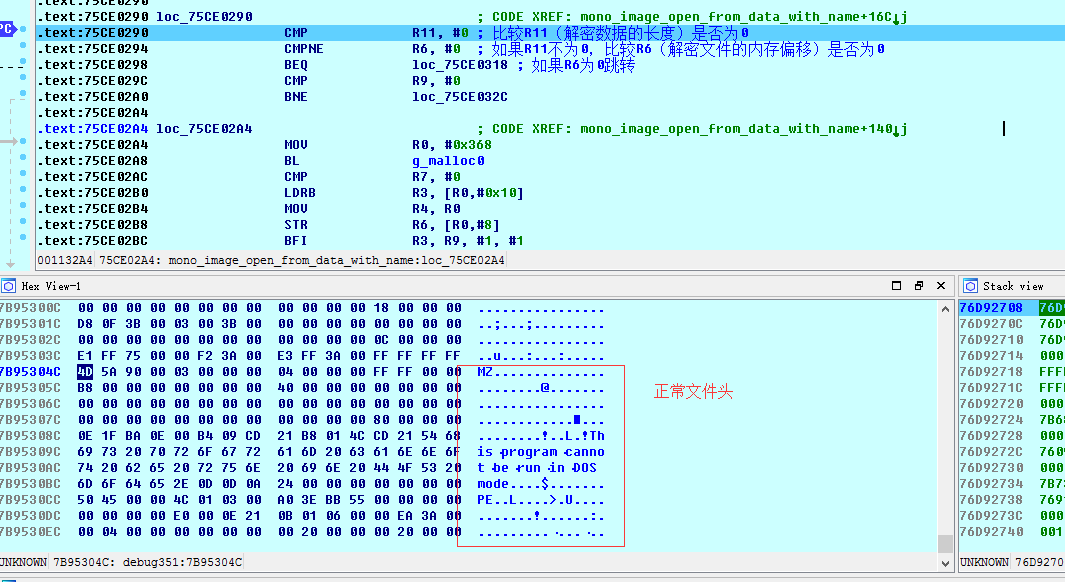
This time it can have a dump,
Check Register Window: Find R6 and R11
The entire file offset start R6 = 7B95304C
End offset address R6 = R11 + 7B95304C + 3AF200 = 7BD0224C
Use; dump dex scripts
Under run on ok
Decryption out the effect,
Attach the original dll and decrypted dll
Credits: xiaobaiyey
reviously I read an article by hook decrypting the encrypted dll Unity3D, recently new to dynamic, so they can try the next through IDA, the same as the shelling, dump the decrypted dll file, try the next, it really can, in here to share under
Requirements:
Tools: IDA6.6. DOWNLOAD LINK
Game: Monthly Dragon knife (just find a game)
Enable USB-debugging in Developer Options
Open lib in IDA:
Unzip lib folder from the APK, drag the file libmono.so to IDA
Several functions mainly in the upper and lower breakpoint (refer mono source )
Code (Text):
mono_image_open_from_data_full
mono_image_open_from_data
mono_image_open_from_data_with_name
In a decryption process can about these function
View the final in front of a function call or mono_image_open_from_data_with_name,
Enable Developer Options:
If Developer Option does not show in settings, follow the steps below.
1. Open Settings > About
2. Then tap “Build number” seven times to enable Developer options....
3. Go back to Settings menu and now you'll be able to see “Developer options” there.
4. Tap it and turn on USB Debugging
Dynamic debugging:
If the app has anti-debugging, you need to skip meals to debug, the following brief dynamic debugging Preparations (there are many online tutorials dynamic debugging)
Get android_server file from IDA PRO 6.6\ida66\dbgsrv or download the file HERE!
Push android_server file to the phone
1:
Code:
adb push android_server /data/local/tmp/
Code:
adb shell
Code:
cd /data/data/tmp/
Code:
chmod 777 android_server
Code:
./android_server
Code:
adb forward tcp:23946 tcp:23946
Code:
adb shell am start -D -n com.huiguan.qinglong.taiqi.dl/com.huiguan.qlyyd.UnityPlayerNativeActivity1.
Code:
adb shell
Code:
ps | grep dl
Code:
adb forward tcp:8700 jdwp:PIDRun app (in the f9 at ifa)
This time, open CMD.exe on Windows and run jdb debugger (Java debugger):
Code:
jdb -connect com.sun.jdi.SocketAttach:hostname=127.0.0.1,port=8700Run app will break on the linker
Then if the app is no anti-molestation: running directly f9
This window appears: same point
Wait a moment, will end on Linker , directly connected to f9 op row
If this window appears, select "yes (pass to app)" without waiting
Many may appear behind all this window select yes and then run f9
Finally broken in the mono_image_open_from_data_with_name, method
Loading is not the first time we want to skip dll
If you can not read f5 look at the source code, source code demonstrate this direct f5, where he rewrote momo source
Code:
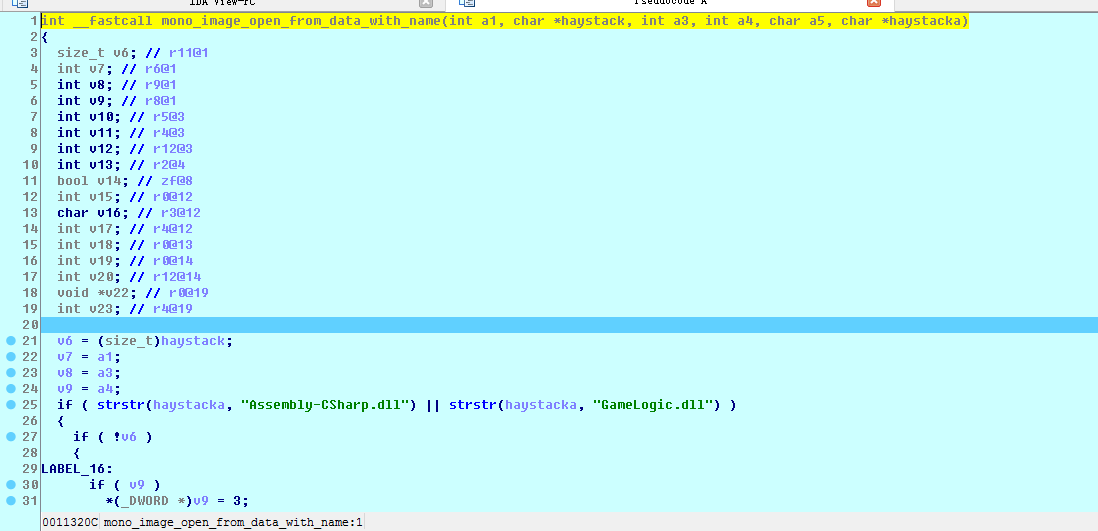
int __fastcall mono_image_open_from_data_with_name (int a1, char * haystack, int a3, int a4, char a5, char * haystacka)
Code:
// NT A1 read dll file offset address
// Char * haystack, DLL file size
// Char * haystacka , file nameThis time following the R1 register to see the encrypted DLL file address, indicating the DLL has not yet begun to decrypt, decryption may later. And laid down the road to change a single note of each register after a simple loop
The dll decrypted
This time it decrypted DLL in memory,
This time it can have a dump,
Check Register Window: Find R6 and R11
The entire file offset start R6 = 7B95304C
End offset address R6 = R11 + 7B95304C + 3AF200 = 7BD0224C
Use; dump dex scripts
Code:
auto fp, dexAddress;
fp = fopen ( "D:\\Test.dll", "wb");
for (dexAddress = 0x7B95304C; dexAddress < 0x7BD0224C; dexAddress ++)
fputc (Byte(dexAddress), FP);Decryption out the effect,
Attach the original dll and decrypted dll
Credits: xiaobaiyey
Last edited:

