I still had 3 years old APKs of a racing game that fake crashes if using resigned APK but wasn't able to bypass it due to lack of cracking skills. Today I try to bypass it.
While comparing both old and new version, I discovered a new folder with 2 smali hidden pretending to be ads at \com\applovin\sdk\applovinsdkattributioninterface\. Attribution.smali is an X509 fingerprint check that checks if the APK's fingerprint match with the original fingerprint stored in-game but where the heck is string of fingerprint and fake crash code?
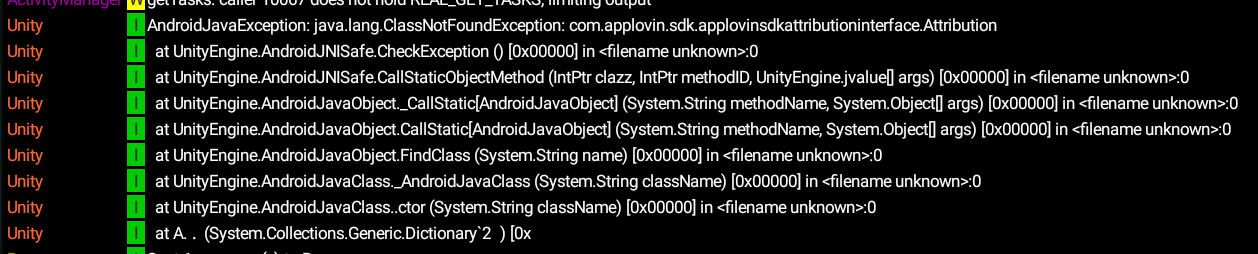
I deleted the folder applovinsdkattributioninterface, compile apk and launch to see what happen. Game gets stuck on black screen. I captured a logcat and got interesting logs
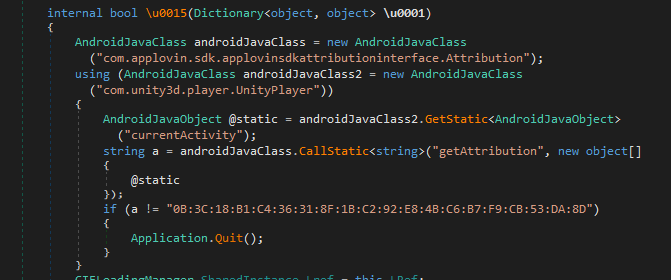
Now I know the signature check and fake crash come from Assembly C# code. After a while of searching I met this code. This code execute Attribution class code to get SHA1 fingerprint and forward data to Unity game. Quit(); is called if fingerprint does not match. Simply remove the whole code or just remove Application.Quit(); in IL editor if you have problem compiling the code
Sample smali code: x509 - Pastebin.com (only useful for code searching purposes)
In the next version, the dev changed the whole X509 check to MD5 file check with KillProcess in the same smali class. It checks if MD5 match with the original or if package name is the same. If not, run KilProcess a.k.a fake crash
The getAttribution(Landroid/content/Context;)Ljava/lang/String; is a string. It can be easly bypassed by returning no string
Smaple smali code: MD5 - Pastebin.com (only useful for code searching purposes)
Credit:
iAndroHacker
While comparing both old and new version, I discovered a new folder with 2 smali hidden pretending to be ads at \com\applovin\sdk\applovinsdkattributioninterface\. Attribution.smali is an X509 fingerprint check that checks if the APK's fingerprint match with the original fingerprint stored in-game but where the heck is string of fingerprint and fake crash code?
I deleted the folder applovinsdkattributioninterface, compile apk and launch to see what happen. Game gets stuck on black screen. I captured a logcat and got interesting logs
Now I know the signature check and fake crash come from Assembly C# code. After a while of searching I met this code. This code execute Attribution class code to get SHA1 fingerprint and forward data to Unity game. Quit(); is called if fingerprint does not match. Simply remove the whole code or just remove Application.Quit(); in IL editor if you have problem compiling the code
Sample smali code: x509 - Pastebin.com (only useful for code searching purposes)
In the next version, the dev changed the whole X509 check to MD5 file check with KillProcess in the same smali class. It checks if MD5 match with the original or if package name is the same. If not, run KilProcess a.k.a fake crash
The getAttribution(Landroid/content/Context;)Ljava/lang/String; is a string. It can be easly bypassed by returning no string
Code:
.locals 1
const-string v0, ""
return-object v0Smaple smali code: MD5 - Pastebin.com (only useful for code searching purposes)
Credit:
iAndroHacker
Last edited:
