Note: This tutorial was created by xiaobaiyey and written in chinese. This tutorial is poorly translated from Google Translation but i have fixed some grammar to make it easier to understand.
How to get the decrypted DLL , through IDA , GDB or directly decryption.
A new gaming platform out of the game (game name omitted), try ida dump the decrypted DLL , (the previous method introduced, as dynamic debugging, you can find information on the Internet)
What happen if you load DLL into Reflector,
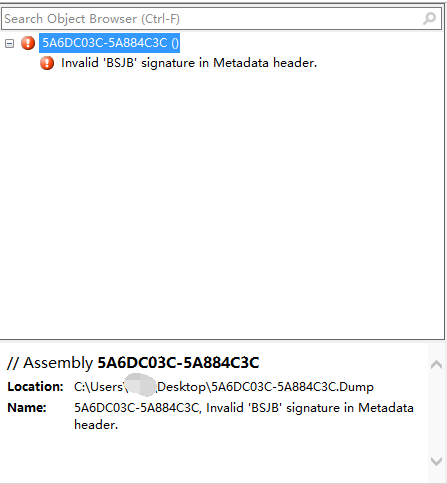
Invalid 'BSJB' Signature in the Metadata header. This error, that is, BSJB this structure there is an error,
I do not know .net file header structure, specifically refer to the article, in recent days, will focus on learning under the net file header structure.
再探.NET的PE文件结构(安全篇) - BattleHeart - 博客园
If you don't have CFF Explorer installed yet, you can download it from here: CFF Explorer
Specifically I do not presented direct demonstration operation, will dump the dll file into CFF Explorer viewMetadata header. structure,
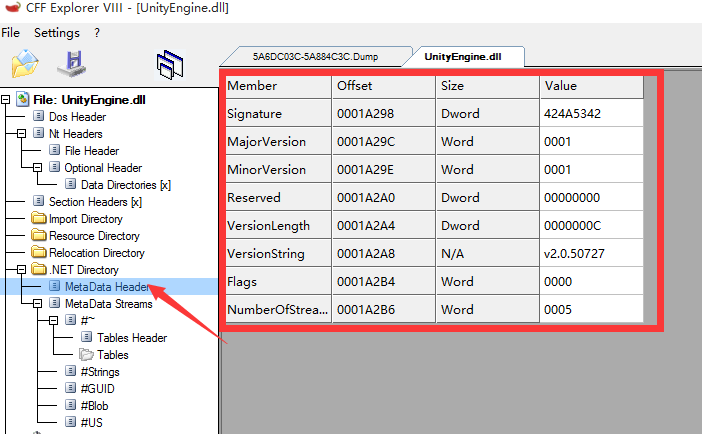
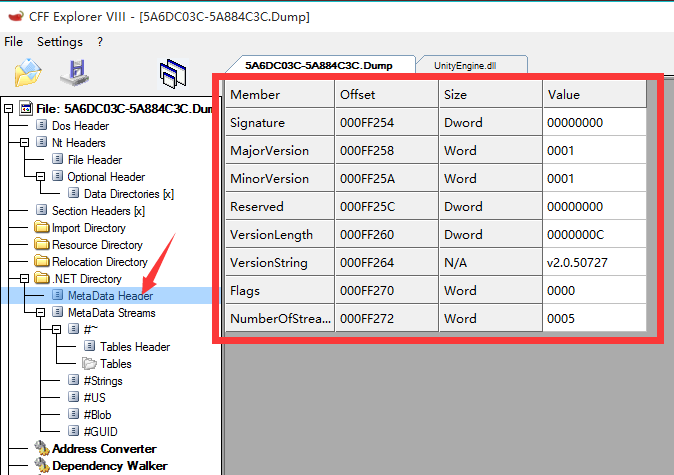
Left to dump out, the right to the normal structure, you can see on the left signature field is cleared, understand net pe file header, it will soon be able to locate BSJB address and fix, Due to the pe file do not know, manual calculation method looked a long time, Leng Shimo understand how to calculate,
I do not analyze, and directly on the tool operation calculation, because we want to view BSJB structure, need to calculate the BSJB address the following method of calculation,
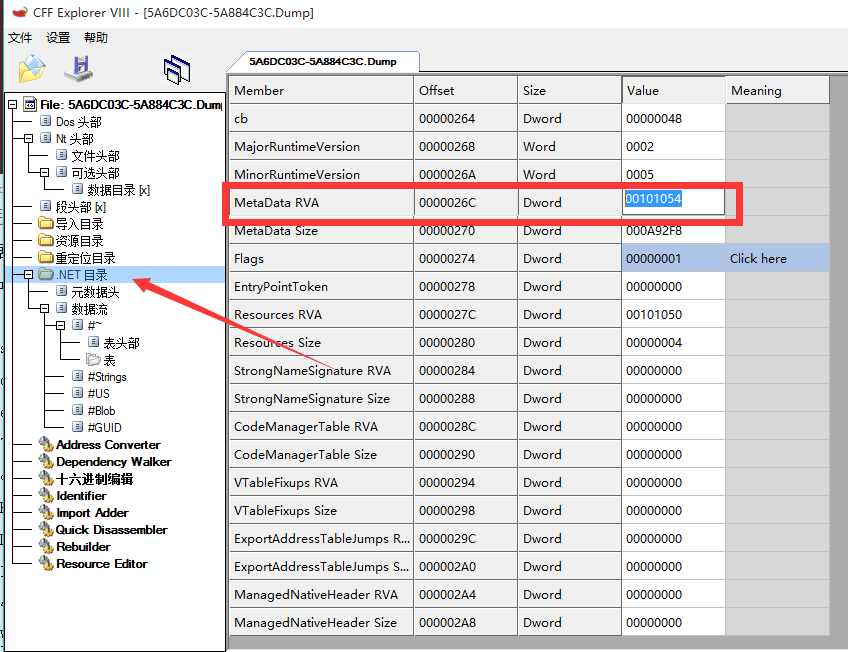
Copy the value: 00101054
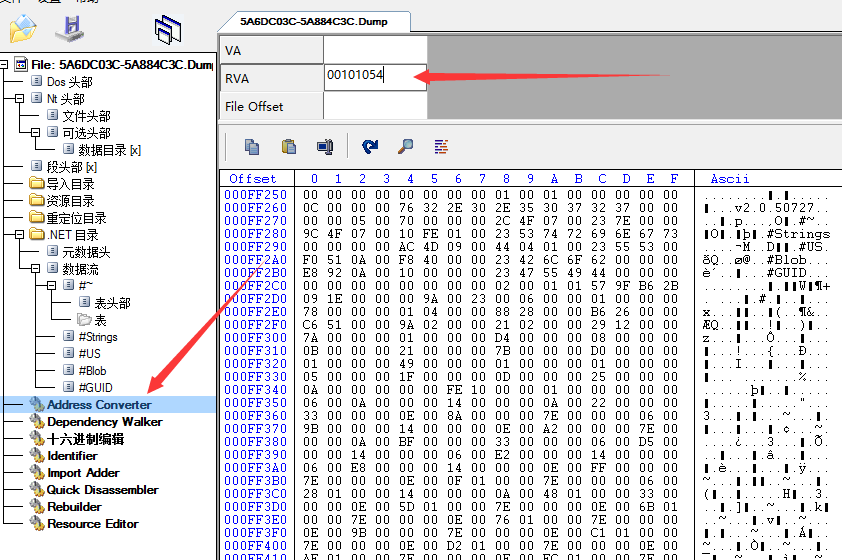
This is when you can look and see BSJB structure, the following is not normal,
And normal comparison:
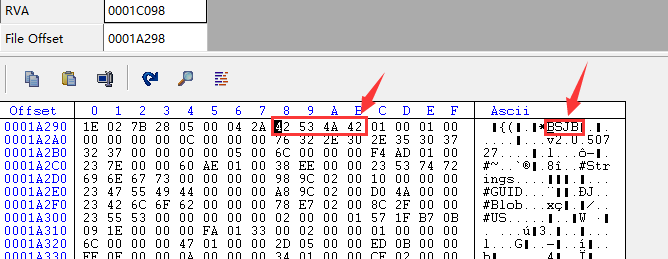
Comparison found dump out dll BSJB structure just entering the string BSJB erased it.
This time, the BSJB hex fill up, you can
00 00 00 00 into 42 53 4A 42 this time, ok drag DLL file into Reflector
Side dishes, the process is relatively simple, because the online description .net pe structure of the article header is not much, provided above blog article analyzes pe header in more detail.
There is, if Meta Data RVA and the Meta the Data
SIZE be erased, you can use the following methods to repair (see Ice Forum by = _ =! );
I forgot the link address.
Navigate to:
1. Nt Headers -> File Header -> Characteristics -> Uncheck "File is a DLL" -> OK
2. Address Converter -> Search "BSJB" find offset "000037AC" -> fill in the "File offest" We got "Meta Data RVA":
RVA = 000047AC
3. .NET Directory -> Meta Data RVA -> Fill was the RVA "000047AC"
4. Optional Header -> the Data in Directories to [X] -> Import Directory the RVA (the Value) -> get " 00006A40 "
Calculate the Meta the Data SIZE:
Meta Data SIZE = Import Directory the RVA - the Meta the RVA the Data 0x6A40
0x47AC = 0x2294
Meta Data RVA= 000047AC
Meta Data SIZE = 00002294
After completion of the above correction operation can be saved!
Tucao the end, the game now encrypted dll Unity3D basically are not difficult, personal feel of the game is to do the anti-gdb debugging and ida or fuss in the structure dll file because dynamic debugging to get the dll is very simple,
On top of a game dll file structure of the processing done, dump out can not be used directly for a repair can be used, there will be an article on the net behind the estimated file header, which make up a few days in this area of knowledge under
Credit:
xiaobaiyey
How to get the decrypted DLL , through IDA , GDB or directly decryption.
A new gaming platform out of the game (game name omitted), try ida dump the decrypted DLL , (the previous method introduced, as dynamic debugging, you can find information on the Internet)
What happen if you load DLL into Reflector,
Invalid 'BSJB' Signature in the Metadata header. This error, that is, BSJB this structure there is an error,
I do not know .net file header structure, specifically refer to the article, in recent days, will focus on learning under the net file header structure.
再探.NET的PE文件结构(安全篇) - BattleHeart - 博客园
If you don't have CFF Explorer installed yet, you can download it from here: CFF Explorer
Specifically I do not presented direct demonstration operation, will dump the dll file into CFF Explorer viewMetadata header. structure,
Left to dump out, the right to the normal structure, you can see on the left signature field is cleared, understand net pe file header, it will soon be able to locate BSJB address and fix, Due to the pe file do not know, manual calculation method looked a long time, Leng Shimo understand how to calculate,
I do not analyze, and directly on the tool operation calculation, because we want to view BSJB structure, need to calculate the BSJB address the following method of calculation,
Copy the value: 00101054
This is when you can look and see BSJB structure, the following is not normal,
And normal comparison:
Comparison found dump out dll BSJB structure just entering the string BSJB erased it.
This time, the BSJB hex fill up, you can
00 00 00 00 into 42 53 4A 42 this time, ok drag DLL file into Reflector
Side dishes, the process is relatively simple, because the online description .net pe structure of the article header is not much, provided above blog article analyzes pe header in more detail.
There is, if Meta Data RVA and the Meta the Data
SIZE be erased, you can use the following methods to repair (see Ice Forum by = _ =! );
I forgot the link address.
Navigate to:
1. Nt Headers -> File Header -> Characteristics -> Uncheck "File is a DLL" -> OK
2. Address Converter -> Search "BSJB" find offset "000037AC" -> fill in the "File offest" We got "Meta Data RVA":
RVA = 000047AC
3. .NET Directory -> Meta Data RVA -> Fill was the RVA "000047AC"
4. Optional Header -> the Data in Directories to [X] -> Import Directory the RVA (the Value) -> get " 00006A40 "
Calculate the Meta the Data SIZE:
Meta Data SIZE = Import Directory the RVA - the Meta the RVA the Data 0x6A40
0x47AC = 0x2294
Meta Data RVA= 000047AC
Meta Data SIZE = 00002294
After completion of the above correction operation can be saved!
Tucao the end, the game now encrypted dll Unity3D basically are not difficult, personal feel of the game is to do the anti-gdb debugging and ida or fuss in the structure dll file because dynamic debugging to get the dll is very simple,
On top of a game dll file structure of the processing done, dump out can not be used directly for a repair can be used, there will be an article on the net behind the estimated file header, which make up a few days in this area of knowledge under
Credit:
xiaobaiyey
