Hello, I currently plan to modify the files that are loaded by this game: HATSUNE MIKU: COLORFUL STAGE! – Applications sur Google Play
My goal is to modify the dialogues which are stored in downloadable files after installing the game.
These files are stored in: /storage/emulated/0/Android/data/com.sega.ColorfulStage.en/files/data
I was able to understand that they were here because when downloading new dialogs files were added to this folder.
In this folder there are many other folders with a tree structure like this:
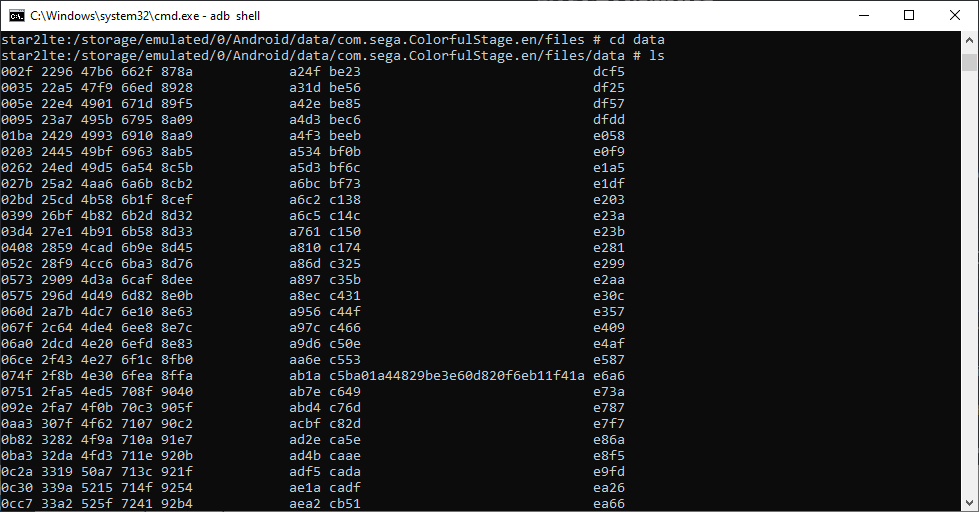
In these folders is one to several files, with names like this:
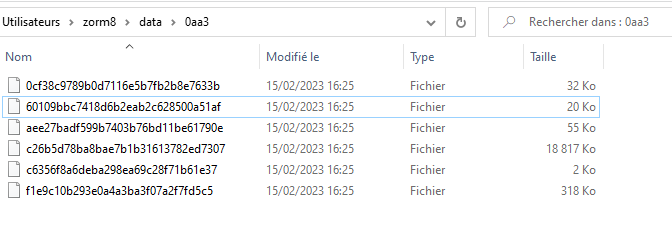
I attach to my post an example file (0b82.rar)

I would like to be able to decrypt these files and encrypt them so as to have in the game a modification of dialogue or image for example.
After research I found that it was surely necessary to decompile using the libil2cpp and global-metadata.dat files and with this find the function which decrypts the file and potentially understand how to do the manipulation manually.
I managed to get a dump.cs with the list of addresses and names of functions in the application, but I don't have the contents of the functions.
I'm not at all sure if I'm on the right track to figure out how to decrypt my files and would like your help in figuring out how to do this.
Thanks to anyone who takes the time to respond to my post.
My goal is to modify the dialogues which are stored in downloadable files after installing the game.
These files are stored in: /storage/emulated/0/Android/data/com.sega.ColorfulStage.en/files/data
I was able to understand that they were here because when downloading new dialogs files were added to this folder.
In this folder there are many other folders with a tree structure like this:
In these folders is one to several files, with names like this:
I attach to my post an example file (0b82.rar)
I would like to be able to decrypt these files and encrypt them so as to have in the game a modification of dialogue or image for example.
After research I found that it was surely necessary to decompile using the libil2cpp and global-metadata.dat files and with this find the function which decrypts the file and potentially understand how to do the manipulation manually.
I managed to get a dump.cs with the list of addresses and names of functions in the application, but I don't have the contents of the functions.
I'm not at all sure if I'm on the right track to figure out how to decrypt my files and would like your help in figuring out how to do this.
Thanks to anyone who takes the time to respond to my post.
Attachments
-
2 MB Views: 94

