Devs don’t know how to secure their game and just blocked rooted device, but the game can be easly hacked which will work on non-rooted devices so it’s pointless to block rooted device. Having a rooted device doesn’t mean you can just hack games, you can do a lot of customization on Android OS. That’s the reason why many peoples root their device and reason why we have XDA community. Devs just don’t understand that.
So let’s get started.
First of all you need:
- IDA Pro (To disassemble .so file)
- Any hex editor (To edit .so file)
- Winrar or 7-zip (Extract files from APK file)
Note: You need to have basic knowledge of IDA and ARM assembly
Root detection usally come from smali but cocos2d have ability to communicate with smali to get root detection data from it.
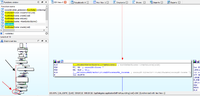
Disassemble libcocos2dcpp.so file
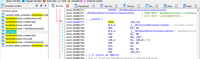
Here is what I found, a Root detection scene that appear a warning screen that root is detected and can’t play. After I analized for a while, RootDetectScene::createScene(void) is only interesting
Hightlight the function, press X to xref and select the first address RootDetectScene::createScene
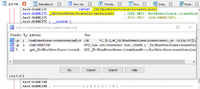
Xref again
IDA showed me this code.
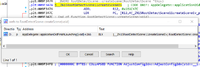
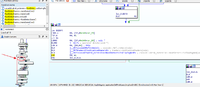
Press SPACEBAR and look at Graph overview. We can see it placed right down at the bottom with a visible red line. We can easly see there is an if-else-statement in the middle of graph
Click on the middle of Graph where the red line come from
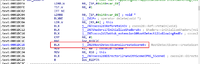
Press F5 to view Pseudocode to understand the code easier. See, there is an if-statement
If you want to look deeper, hightlight on isGlowingRed(v42) and press ENTER. You do it 5 times
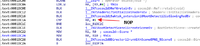
isGlowingRed(v42) -> isGlowingRed(this); -> j_j_isGlowingRedJni(this); -> j_isGlowingRedJni((int)this); isGlowingRedJni();
and you will reach this code. Here it gets boolean data from isGlowingRed from smali location “jp/aktsk/cocos2dx/extension/RootDetect”
Go back to AppDelegate::applicationDidFinishLaunching.
We want to replace CMP R0, #1 to NOP
Open any hex editor, go to the offset of CMP R0, #1 you found and replace it with 00 BF (NOP)
That’s all. You have bypassed the root warning message
Credit:
AndnixSH#
Attachments
-
48.8 KB Views: 224
-
28.6 KB Views: 213
-
25 KB Views: 210
-
29.2 KB Views: 235
-
68.6 KB Views: 193
-
58.1 KB Views: 221
-
15.5 KB Views: 228
-
15.9 KB Views: 217
-
22 KB Views: 204
Last edited: