dingdingdong
Platinian
The main purpose of this thread is to introduce you about another method or way in hacking android games.
This simple way of hacking will help you to avoid some detection that most of dev put in their code, like detecting the originality of the apk and their libs which usually the common stuff that got modded or edited. Like what? checking apk or libs hash and signature then the dev can put an action to your game, like flagging your id or prevent you to play their game. This method also prevent Lib Injection for hooking or internal memory patching.
Here the first stuff you need to do :
- Install GameGuardian (and Virtual Space for non-rooted phone).
- Dumped il2cpp offset and knowledge of basic il2cpp modding, go here if you didn't know what is this part : Modding libil2cpp.so games tutorial for beginners with Video Tutorial - Platinmods.com - Android & iOS MODs, Mobile Games & Apps
Steps :
1. Creating GameGuardian Lua script to patching our offset.
2. Getting DWORD value or convert armv7 hex code to DWORD
You notice that there's this minus decimal numbers, like -476053504 or -476053503 and -476052991, what is that? and how to get that number?
That minus number or value is basically armv7 hex code that converted to decimal or DWORD in GameGuardian.
- So, first get your hex code, ex: returning 1 or true is "01 00 A0 E3". We just need the first 4 byte, because return or "1E FF 2F E1" is -516948194 in DWORD and won't change unless you were modding an ARM64 lib.
- Go to this website Online Hex Converter - Bytes, Ints, Floats, Significance, Endians - SCADACore to convert hex code to DWORD or INT32 - Little Endian (DCBA) in that website.
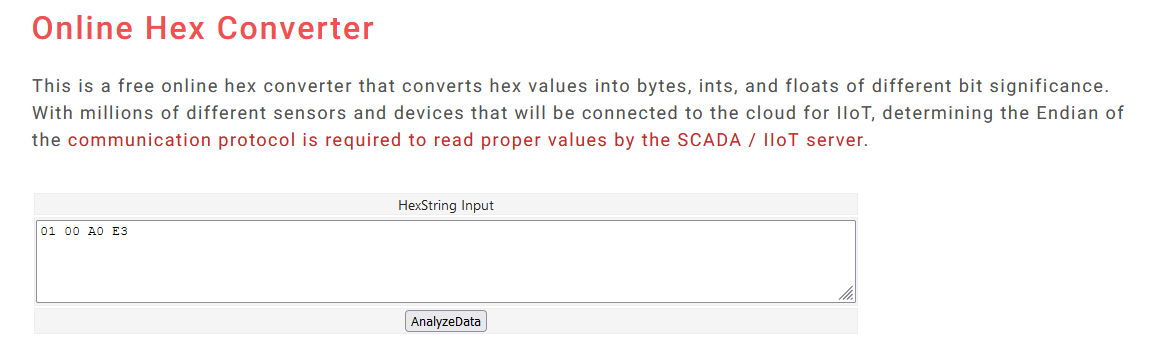
- Put your hex code into HexInput String box and click the AnalyzeData button, like this
- Next, scroll down until you see " INT32 - Little Endian (DCBA) " Table, like this
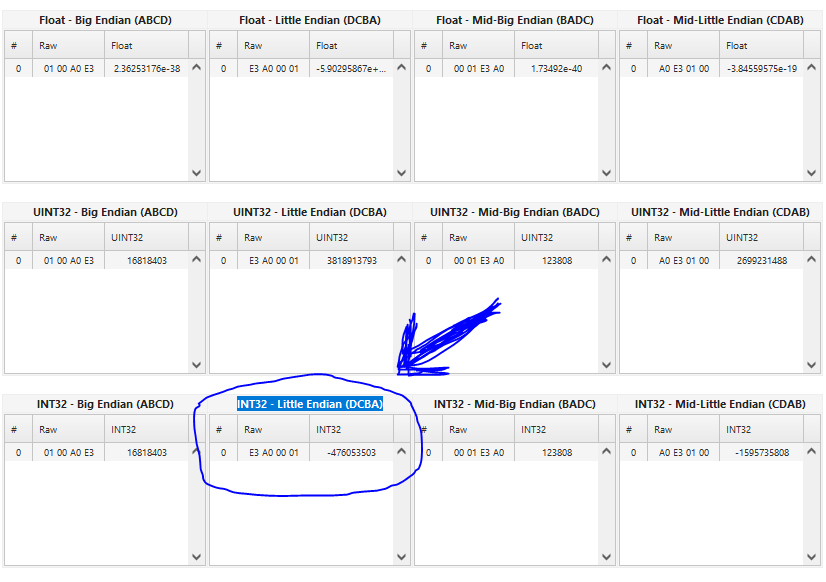
- And finally, copy that IN32 number.
Q&A
- What is the profit from this method? Well if you using a rooted phone, you can play with original apk from playstore and login or bind using google account.
- What if i'm using non-rooted? Use this Virtual Space Multiple Accounts + Assist - Virtual spaces (no root) - GameGuardian , this one support google play service
- Why bother with this if you can make mod menu? Like i explain earlier, there's a lot of ways to detect hacks or cheats, and mostly modding tutorial on the internet are required to decompile the apk first and injecting or editing lib files, which are easily to detect, and btw some dev actually just flag you instead of preventing or banning you in the first place so they can keep the new player rate rising up for ads, then ban you later or the next day after giving you hope and wasting your time, LMAO.
- What if i use ARM64 instead or ARMv7? Just use ARM64 hex code and convert it.
ATTENTION!!!
I'm NOT gonna reply to a stupid question, like "i CaN't InStAlL GaMeGuArDiAn / ViRtUaL sPaCe" or "CaN yOu MaKe ScRiPt FoR tHiS gAme".
If you can't install those apps, use google to solve your problem since that apps is also exist when you google it!
I post a TUTORIAL THREAD, not an open request or service to spoon feed your lazy ass.
BUT!!!
I will reply to the question about the code because i write it myself.
This simple way of hacking will help you to avoid some detection that most of dev put in their code, like detecting the originality of the apk and their libs which usually the common stuff that got modded or edited. Like what? checking apk or libs hash and signature then the dev can put an action to your game, like flagging your id or prevent you to play their game. This method also prevent Lib Injection for hooking or internal memory patching.
Here the first stuff you need to do :
- Install GameGuardian (and Virtual Space for non-rooted phone).
- Dumped il2cpp offset and knowledge of basic il2cpp modding, go here if you didn't know what is this part : Modding libil2cpp.so games tutorial for beginners with Video Tutorial - Platinmods.com - Android & iOS MODs, Mobile Games & Apps
Steps :
1. Creating GameGuardian Lua script to patching our offset.
Code:
-- hide/minimize GameGuardian after run the script
gg.setVisible(false)
-- put a toast message to tell that patching is on progress
gg.toast('-=[ PATCHING ]=-')
-- this function is used to patch an "get" or "return" function
function patch8bytes(pAddress, pValue)
-- get the base address of lib2ilcpp.so
local soBase = gg.getRangesList('libil2cpp.so')[1].start
-- patching the first 4 bytes for our value, ex : mov r0, #100 (yes, this line of code need 4 bytes in memory)
gg.addListItems({
[1] = {
address = soBase + pAddress,
flags = gg.TYPE_DWORD,
value = pValue,
freeze = true
}
})
-- after put our desired value, we need to put an return, ex : BX LR. So just add "4" to the first address
-- BX LR
gg.addListItems({
[1] = {
address = soBase + pAddress + 4,
flags = gg.TYPE_DWORD,
value = -516948194,
freeze = true
}
})
gg.removeListItems(gg.getListItems())
end
-- this function is used to patch an void function, ex: skipping an decreament or checking function
function patch4bytes(pAddress)
local soBase = gg.getRangesList('libil2cpp.so')[1].start
-- no need another extra 4 bytes, because we just need to return
-- BX LR
gg.addListItems({
[1] = {
address = soBase + pAddress,
flags = gg.TYPE_DWORD,
value = -516948194,
freeze = true
}
})
gg.removeListItems(gg.getListItems())
end
-- usage how to patch the offset from our dumped il2cpp
-- returning true or false
ofs_IsLocked = 0x11AA22B
patch8bytes(ofs_IsLocked, -476053504) -- return 0 or false
ofs_HasSkin = 0x11AA22B
patch8bytes(ofs_IsLocked, -476053503) -- return 1 or true
-- returning big value
ofs_GetMoney = 0x11AA22B
patch8bytes(ofs_GetMoney, -476052991) -- return 10000000
-- skipping a function or force return
ofs_SubtractMoney = 0x11AA22B
patch4bytes(ofs_SubtractMoney) -- skip or force the function to return, ex: Freezing money when being used
-- put a toast message when completed
gg.toast('-=[ COMPLETE ]=-')
-- stop the script
os.exit()2. Getting DWORD value or convert armv7 hex code to DWORD
You notice that there's this minus decimal numbers, like -476053504 or -476053503 and -476052991, what is that? and how to get that number?
That minus number or value is basically armv7 hex code that converted to decimal or DWORD in GameGuardian.
- So, first get your hex code, ex: returning 1 or true is "01 00 A0 E3". We just need the first 4 byte, because return or "1E FF 2F E1" is -516948194 in DWORD and won't change unless you were modding an ARM64 lib.
- Go to this website Online Hex Converter - Bytes, Ints, Floats, Significance, Endians - SCADACore to convert hex code to DWORD or INT32 - Little Endian (DCBA) in that website.
- Put your hex code into HexInput String box and click the AnalyzeData button, like this
- Next, scroll down until you see " INT32 - Little Endian (DCBA) " Table, like this
- And finally, copy that IN32 number.
Q&A
- What is the profit from this method? Well if you using a rooted phone, you can play with original apk from playstore and login or bind using google account.
- What if i'm using non-rooted? Use this Virtual Space Multiple Accounts + Assist - Virtual spaces (no root) - GameGuardian , this one support google play service
- Why bother with this if you can make mod menu? Like i explain earlier, there's a lot of ways to detect hacks or cheats, and mostly modding tutorial on the internet are required to decompile the apk first and injecting or editing lib files, which are easily to detect, and btw some dev actually just flag you instead of preventing or banning you in the first place so they can keep the new player rate rising up for ads, then ban you later or the next day after giving you hope and wasting your time, LMAO.
- What if i use ARM64 instead or ARMv7? Just use ARM64 hex code and convert it.
ATTENTION!!!
I'm NOT gonna reply to a stupid question, like "i CaN't InStAlL GaMeGuArDiAn / ViRtUaL sPaCe" or "CaN yOu MaKe ScRiPt FoR tHiS gAme".
If you can't install those apps, use google to solve your problem since that apps is also exist when you google it!
I post a TUTORIAL THREAD, not an open request or service to spoon feed your lazy ass.
BUT!!!
I will reply to the question about the code because i write it myself.
Last edited:
