Theeundertakeer
Platinian
Good day dear friends. My last post was very interesting for quite few people so if you still didn't check my post regarding Rooted way of using FRIDA you can do so by following this link . So now let's get started! This tutorial will be from 0 to 100 with all nuance and details I came across.
Let's start from setting up our Python Envo.
1. Download Python
* Don't forget to tick "Add to system variables" while inside installation flow otherwise you won't be able to use Python through CMD and will be coming to comments section :)
2. After which download PIP or by entering in the command line
*This is required to install our FRIDA tools on your machine
1. This is the easiest way to install FRIDA, just type in your command line
Now we have most items up and running but still we need couple more.
Let's get started with APK Decompiler
1. The far-most convenient way of decompiling APK is to use APK Eeasy Tool GUI so download it.
Now at this point there is only 1 single download left...
Let's get started with FRIDA Gadget library download
1. Navigate to the link
2. Pick 16.1.5 (Latest version as of this writing)
3. Click on Show All 262 assets
4. Look for frida-gadget-16.1.5-android-arm64.so.xz (99.99% of the time you will need arm64 as this is the architecture for our popular Android devices)
5. Finally download it.
Optional but desired:
1. Download latest Android Studio and install it.
2. After downloading open it up, click on settings, go to plugins and go to Marketplace
3. Search for java2smali. You can follow this link for more info or straight install.
4. Install the plugin and create some empty project
5. Create some empty JAVA file NOT KOTLIN
6. Write some Java code, find Build, Convert Java to smali or right click inside your java file and choose ASM bytecode smali viewer
*This will be your closest friend as you will be able to inject smali code into some native made apps without any hassle or worries, just write your java code, convert to smali and copy paste
Fun part begins!
1. Download any victim (APK surely :) )
2. Open APK Easy Tool GUI
3. Drag and drop your APK file into the picker box as shown in the image
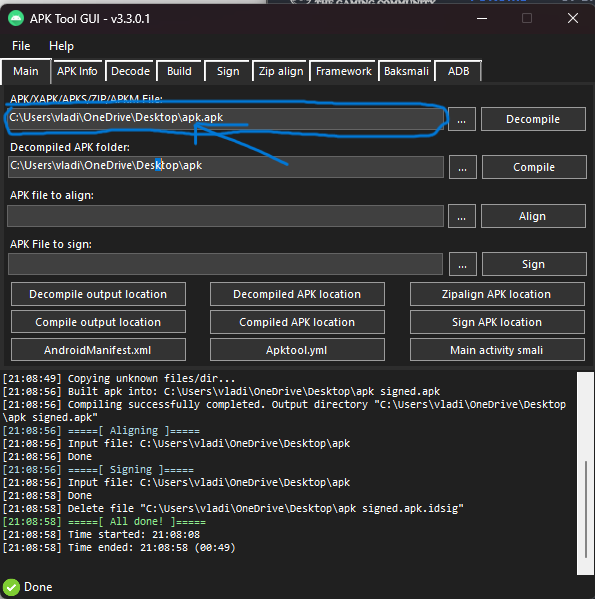
4. Decompilation will start automatically, wait for it to finish
Injecting Frida Gadget into APK libs
Do you remember our frida-gadget-arm64 file we downloaded? yes yes, extract it and get the .so file out of it.
Now we need to inject this file into APK structure so our APK can listen to our hooks and injections.
1. After successful decompilation, you will see a folder with the same name as your APK file which will be just in the same location you have your victim APK
2. Navigate to that folder and then to "yourDecompiledFolder/lib/arm64-v8a/" , as usual, we need only 64 bit structure as we know why.
3. Grab your frida-gadget.so or whatever name it has, the most important is that it has to have .so extension
4. Copy your .so file into the final path described in the 2nd step, and most importantly APPEND "LIB" TO THE BEGGINGIN OF FILE NAME , so frida-gadget.so will will now be libfrida-gadget.so
* For now we done , yet even more interesting part is coming, INJECTION OF SMALI
Inject Library Load Into Java Code
So now we have to inject some code to make our newly moved library create a tcp connection and listen for our own connection
The most easiest way to copy past the smali lines I will be putting, or you can use Android Studio as described to generate smali code.
1. Find Launcher activity, if you can find some class which extends Application base class, even better.
2. To be able to find it navigate to your decompiled root folder and find AndroidManifest.xml file, open it.
3. User your favourite IDEA or code editor and look for this kind of a code
This will be your launcher activity, go a little up in your editor where it says
and this will be your launcher activity, usualy it is always 1 line above <intent-filter>
4. Take a note of it package name and path.
5. Go to your decompiled folder and navigate by that path, for example if I found that my launcher activity is "com.google.firebase.MessagingUnityPlayerActivity" then my path to that file from decompiled folder will be "com/google/firebase/MessagingUnityPlayerActivity" and don't be afraid if that's a library name not some custom name, that's fine, launcher can be any kind of a class
6. After finding our MessagingUnityPlayerActivity file we will open it to edit, so open it.
Followng steps are super imporant to be precious!
1. After you opened MessagingUnityPlayerActivity copy and paste this followng code after the comment which says # direct methods:
Explanation of the above code :
It is literally means this JAVA representation :
As you can notice we didn't add lib to the beggining and that's how it has to be! For the filename it has to have lib at the beggining but inside the code we write name after lib appendix and without .so extension.
So far you are rockstar!
Getting device ready
1. Open your device developer settings (if missing tap the build number from OS info 7 times and woala), find USB DEBUGGING and turn it on
2. Download this small tool called Minimal ADB required to get some useful info for our device which we will be using, like device number. Latest version is 1.4.3 as of now.
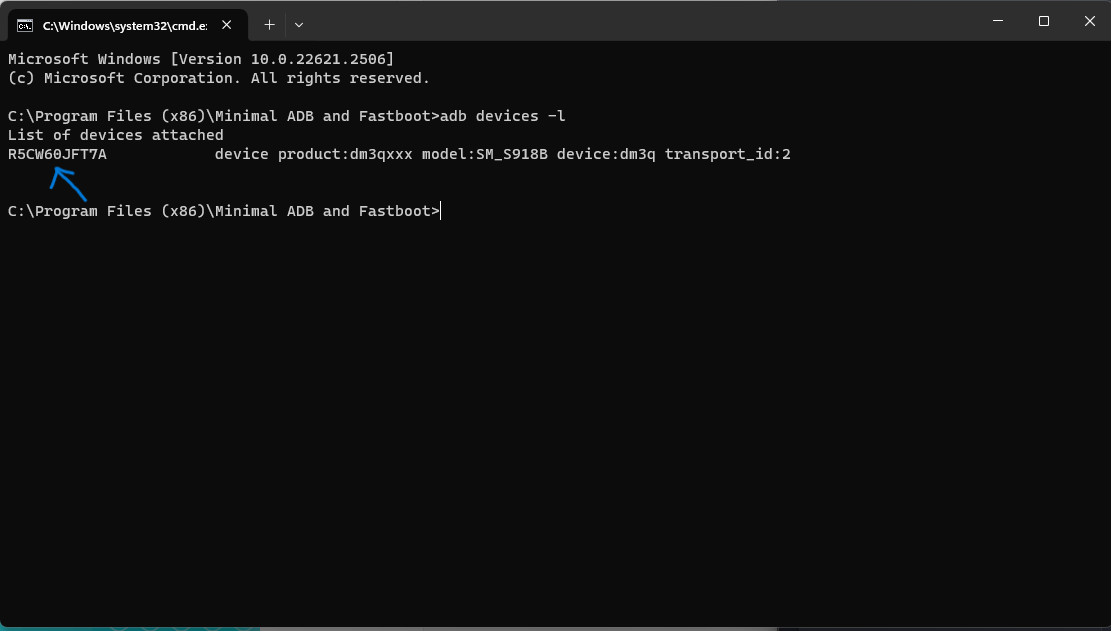
3. Connect your device to your PC or laptop, open Minimal ADB and Fastboot programm and type "adb devices -l " which have to bring a confirmation dialog on your phone.
4. Check the mark to alow always and click Allow
5. Take a note of your device id as shown in the screenshot below
Dumping DLL files
1. Download DnSpyprogramm
2. Download LL2Cpp Dumper
3. Open LL2CPP Dumper
4. Pick first file as "libil2cpp.so" which shall be by path of "yourDecompiledFolder/lib/arm64-v8a/"
5. Pick second file as global-metadata.dat which shall be under the path of "yourDecompiledFolder/assets/bin/Data/Managed/Metadata/"
6. Wait untill it says click to continue , make the click!
7. Decompiled DLL files will be in the folder called "DummyDLL" which shall be right in the root folder where you have your LL2CPP dumper
8. Open DnSpy programm
7. Copy all files from DummyDLL folder and drag drop into left file explorer of DnSpy programm
8. Search for your desired thing!
Prepairing Attack
We are pretty much half way through now, couple things left to get us going.
1. Recompile your decompiled folder: just drag and drop your folder into second box picker as shown in the screenshot
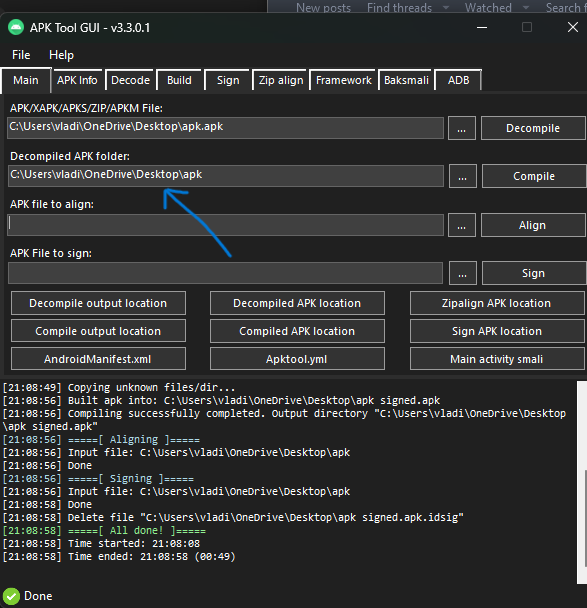
2. It will automatically start compilation process and all subsequent actions to give your ready to install APK. Apk will be in the same place where you have your decompiled folder (not inside decompiled folder)
3. Transfer your APK to your device and install it but don't run it yet.
* After having gone so far, you will notice that while opening your app, even though I told you not :D, will do nothing , simply because our app will now be waiting for any incoming connections from FRIDA on our PC
Hooking to Function
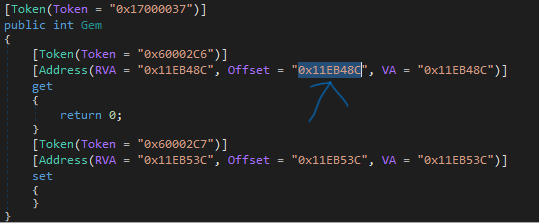
So far we got almost finished, now left to find our needed vulnerabilities and hook to them. Let's say you found function called get_Gem from DLL file we dumped, you will need to :
1. Take a note of the offset like in the screenshot :
2. Create file with .js extension (Find the file in the attachments for your use called GemHack.zip) :
3. Write some code, here is the example :
* As you can see I have prepared for you a variable called offsetAddress , this is what you will need to change to an address you have found in previous steps from DLL file .
* Last but not least you can see I also prepared for you changer , retval.replace(1000000) changs the value and exits the function returning our changed value so my gems will be now 1000000, you can do same for string, like so retval.replace("1000000")
Final Act
1. By now you shall have modified APK on your device, your device connected to PC with the note of the device id
2. Open terminal and type in the following command :
* As you can notice, we don't specify anything but "Gadget" it is because now our app has separate process from FRIDA called "Gadget" which is waiting for connection . Also as you noticed for argument of -l you need to pass a full path to your script.js, I personally just drag and drop the file into terminal so the full path to the file will be correct.
3. Finally hit enter and wait for the magic !
4. At this point your app will launch and you can change your script.js content real time dynamically without worrying about reattaching process again, just update the file and do CTRL+S and that's it your changes are saved and published.
Thank you for your time and happy hacking!
DOWNLOAD
Let's start from setting up our Python Envo.
1. Download Python
* Don't forget to tick "Add to system variables" while inside installation flow otherwise you won't be able to use Python through CMD and will be coming to comments section :)
2. After which download PIP or by entering in the command line
Code:
python get-pip.py*This is required to install our FRIDA tools on your machine
* Important notice is that you will need WINDOWS to get out of most hassle
Let's get started with FRIDA1. This is the easiest way to install FRIDA, just type in your command line
Code:
pip install frida-toolsNow we have most items up and running but still we need couple more.
Let's get started with APK Decompiler
1. The far-most convenient way of decompiling APK is to use APK Eeasy Tool GUI so download it.
Now at this point there is only 1 single download left...
Let's get started with FRIDA Gadget library download
1. Navigate to the link
2. Pick 16.1.5 (Latest version as of this writing)
3. Click on Show All 262 assets
4. Look for frida-gadget-16.1.5-android-arm64.so.xz (99.99% of the time you will need arm64 as this is the architecture for our popular Android devices)
5. Finally download it.
Optional but desired:
1. Download latest Android Studio and install it.
2. After downloading open it up, click on settings, go to plugins and go to Marketplace
3. Search for java2smali. You can follow this link for more info or straight install.
4. Install the plugin and create some empty project
5. Create some empty JAVA file NOT KOTLIN
6. Write some Java code, find Build, Convert Java to smali or right click inside your java file and choose ASM bytecode smali viewer
*This will be your closest friend as you will be able to inject smali code into some native made apps without any hassle or worries, just write your java code, convert to smali and copy paste
Fun part begins!
1. Download any victim (APK surely :) )
2. Open APK Easy Tool GUI
3. Drag and drop your APK file into the picker box as shown in the image
4. Decompilation will start automatically, wait for it to finish
Injecting Frida Gadget into APK libs
Do you remember our frida-gadget-arm64 file we downloaded? yes yes, extract it and get the .so file out of it.
Now we need to inject this file into APK structure so our APK can listen to our hooks and injections.
1. After successful decompilation, you will see a folder with the same name as your APK file which will be just in the same location you have your victim APK
2. Navigate to that folder and then to "yourDecompiledFolder/lib/arm64-v8a/" , as usual, we need only 64 bit structure as we know why.
3. Grab your frida-gadget.so or whatever name it has, the most important is that it has to have .so extension
4. Copy your .so file into the final path described in the 2nd step, and most importantly APPEND "LIB" TO THE BEGGINGIN OF FILE NAME , so frida-gadget.so will will now be libfrida-gadget.so
* For now we done , yet even more interesting part is coming, INJECTION OF SMALI
Inject Library Load Into Java Code
So now we have to inject some code to make our newly moved library create a tcp connection and listen for our own connection
The most easiest way to copy past the smali lines I will be putting, or you can use Android Studio as described to generate smali code.
1. Find Launcher activity, if you can find some class which extends Application base class, even better.
2. To be able to find it navigate to your decompiled root folder and find AndroidManifest.xml file, open it.
3. User your favourite IDEA or code editor and look for this kind of a code
XML:
<intent-filter>
<action android:name="android.intent.action.MAIN"/>
<category android:name="android.intent.category.LAUNCHER"/>
</intent-filter>
XML:
<activity android:name = "com.somepackage.SomeActivity"4. Take a note of it package name and path.
5. Go to your decompiled folder and navigate by that path, for example if I found that my launcher activity is "com.google.firebase.MessagingUnityPlayerActivity" then my path to that file from decompiled folder will be "com/google/firebase/MessagingUnityPlayerActivity" and don't be afraid if that's a library name not some custom name, that's fine, launcher can be any kind of a class
6. After finding our MessagingUnityPlayerActivity file we will open it to edit, so open it.
Followng steps are super imporant to be precious!
1. After you opened MessagingUnityPlayerActivity copy and paste this followng code after the comment which says # direct methods:
Code:
.method static constructor <clinit>()V
.registers 1
.prologue
.line 8
const-string v0, "frida-gadget"
invoke-static {v0}, Ljava/lang/System;->loadLibrary(Ljava/lang/String;)V
.line 9
return-void
.end methodExplanation of the above code :
It is literally means this JAVA representation :
Java:
static {
System.loadLibrary("frida-gadget");
}As you can notice we didn't add lib to the beggining and that's how it has to be! For the filename it has to have lib at the beggining but inside the code we write name after lib appendix and without .so extension.
So far you are rockstar!
Getting device ready
1. Open your device developer settings (if missing tap the build number from OS info 7 times and woala), find USB DEBUGGING and turn it on
2. Download this small tool called Minimal ADB required to get some useful info for our device which we will be using, like device number. Latest version is 1.4.3 as of now.
3. Connect your device to your PC or laptop, open Minimal ADB and Fastboot programm and type "adb devices -l " which have to bring a confirmation dialog on your phone.
4. Check the mark to alow always and click Allow
5. Take a note of your device id as shown in the screenshot below
Dumping DLL files
1. Download DnSpyprogramm
2. Download LL2Cpp Dumper
3. Open LL2CPP Dumper
4. Pick first file as "libil2cpp.so" which shall be by path of "yourDecompiledFolder/lib/arm64-v8a/"
5. Pick second file as global-metadata.dat which shall be under the path of "yourDecompiledFolder/assets/bin/Data/Managed/Metadata/"
6. Wait untill it says click to continue , make the click!
7. Decompiled DLL files will be in the folder called "DummyDLL" which shall be right in the root folder where you have your LL2CPP dumper
8. Open DnSpy programm
7. Copy all files from DummyDLL folder and drag drop into left file explorer of DnSpy programm
8. Search for your desired thing!
Prepairing Attack
We are pretty much half way through now, couple things left to get us going.
1. Recompile your decompiled folder: just drag and drop your folder into second box picker as shown in the screenshot
2. It will automatically start compilation process and all subsequent actions to give your ready to install APK. Apk will be in the same place where you have your decompiled folder (not inside decompiled folder)
3. Transfer your APK to your device and install it but don't run it yet.
* After having gone so far, you will notice that while opening your app, even though I told you not :D, will do nothing , simply because our app will now be waiting for any incoming connections from FRIDA on our PC
Hooking to Function
So far we got almost finished, now left to find our needed vulnerabilities and hook to them. Let's say you found function called get_Gem from DLL file we dumped, you will need to :
1. Take a note of the offset like in the screenshot :
2. Create file with .js extension (Find the file in the attachments for your use called GemHack.zip) :
3. Write some code, here is the example :
JavaScript:
var offsetAddress = 0x11EB48C
var func_ptr =Module.findBaseAddress('libil2cpp.so').add(offsetAddress )
Interceptor.attach(func_ptr, {
onEnter: function (args) {
console.log("method was called called")
},
onLeave: function (retval) {
console.log("exiting method and returning value ")
retval.replace(1000000)
}
})* As you can see I have prepared for you a variable called offsetAddress , this is what you will need to change to an address you have found in previous steps from DLL file .
* Last but not least you can see I also prepared for you changer , retval.replace(1000000) changs the value and exits the function returning our changed value so my gems will be now 1000000, you can do same for string, like so retval.replace("1000000")
Final Act
1. By now you shall have modified APK on your device, your device connected to PC with the note of the device id
2. Open terminal and type in the following command :
Code:
frida -D yourDeviceId -l path\to\your\script.js -U Gadget* As you can notice, we don't specify anything but "Gadget" it is because now our app has separate process from FRIDA called "Gadget" which is waiting for connection . Also as you noticed for argument of -l you need to pass a full path to your script.js, I personally just drag and drop the file into terminal so the full path to the file will be correct.
3. Finally hit enter and wait for the magic !
4. At this point your app will launch and you can change your script.js content real time dynamically without worrying about reattaching process again, just update the file and do CTRL+S and that's it your changes are saved and published.
Thank you for your time and happy hacking!
DOWNLOAD
Last edited by a moderator:




