pentarix1996
Platinian
Good morning. I'm trying to make a mod for the game "Pixel Heroes: Tales of Emond". The first thing I did was obtain the APK, which to my surprise was divided into several parts (something normal for large games). What I did was the following.
adb shell pm path com.haoplay.game.and.hero
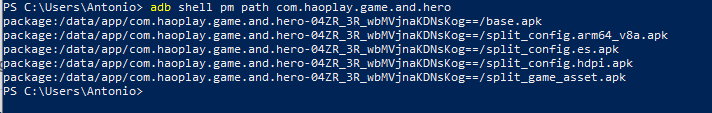
After obtaining 5 routes (as shown in the attached image) I did a pull "adb pull <path> <destination>". When extracting the content of each APK, I saw that in the APK "split_game_asset.apk" there is all the code in .lua. When trying to see the content of each file, I saw that it was encrypted...
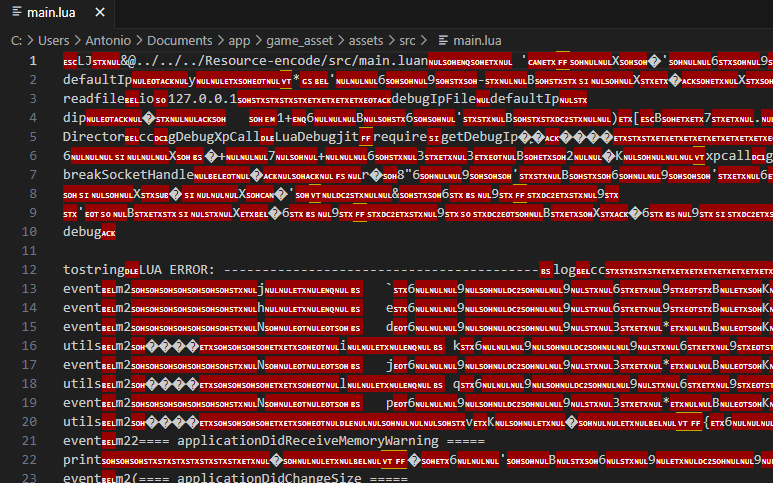
I have previously tried to make mods in other games (made in Unity) with success. But I have never faced one made with LUA. Any suggestions on how to decrypt these files or if I am making a mistake when obtaining the source code?
As an additional note for hexadecimal code changes I use HxD. On the other hand, I tried to do my own research before opening this post, but I can't find anything that helps me :S
Any suggestions on where to go or what to do?
Thanks in advance.
Edit:
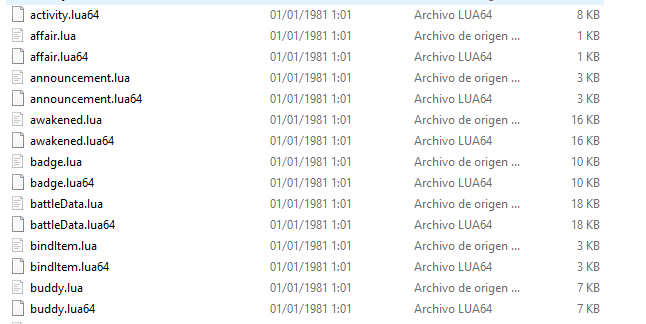
One strange thing that I see and I don't understand very well is why both .lua and .lua64 files appear.
adb shell pm path com.haoplay.game.and.hero
After obtaining 5 routes (as shown in the attached image) I did a pull "adb pull <path> <destination>". When extracting the content of each APK, I saw that in the APK "split_game_asset.apk" there is all the code in .lua. When trying to see the content of each file, I saw that it was encrypted...
I have previously tried to make mods in other games (made in Unity) with success. But I have never faced one made with LUA. Any suggestions on how to decrypt these files or if I am making a mistake when obtaining the source code?
As an additional note for hexadecimal code changes I use HxD. On the other hand, I tried to do my own research before opening this post, but I can't find anything that helps me :S
Any suggestions on where to go or what to do?
Thanks in advance.
Edit:
One strange thing that I see and I don't understand very well is why both .lua and .lua64 files appear.
Last edited:
