This tutorial was been deleted from original source but it's now archived here!
CPAntiDumper created by Caoyin is a tool that obfuscate binary files and .dylibs and prevent others from dumping offsets. It support ARMv7 and ARM64 iOS Binary and Android ARM binaries. ARM THUMB and x86 are currently not supported yet.
Note: CPAntiDumper will not prevent IDA Pro from disassembling
Download:
How to use:
For ease of use, DiDA have included a CPAD.bat file inside the download link below which simplifies the whole process by simply dragging your binary file to the .bat file and reading the on-screen instructions. Of course, you can modify the .bat to your liking. You will also need to edit it to add the location of cpad.exe on your computer. Example usage of CPAD.bat file.
NOTE CPAD is only a Windows tool but will likely work on other operating systems with Wine since it's a simple CLI.
If you would like to run CPAD using cmd, you can do so using this command:
cpad.exe BINARYFILENAME VALUE ARCH
iOS Examples:
Android Example:
Once you run the command, CPAD will analyze the binary and start obfuscating it thus preventing Binary Compare.
Once CPAD completes the process, it will generate 2 new files. BINARYNAME(.so)obf & BINARYNAME.txt
BINARYNAME(.so)obf will be the obfuscated binary file you will need to use. Rename the file and place it back into your IPA/APK and test/share your hack.
BINARYNAME(.so).txt will be the file that contains all the writeData instructions for you to implement inside your Tweak.xm. Most effective way to integrate all the writeDatas inside the .txt to your Tweak.xm is by placing your real writeData in a random place amongst all the other CPAD writeDatas. So if someone tries to dump your offsets, they will have to go through <YOURVALUE> (20,000 other writeDatas for example). This is only for iOS .deb hacks.
Example:
Remember! You can go crazy with your value by entering 100000 into CPAD which will make it super secure but will likely take a lot of time depending on your computer.
NOTE: For CPAD to be more efficient. Use it AFTER you have modded your binary.
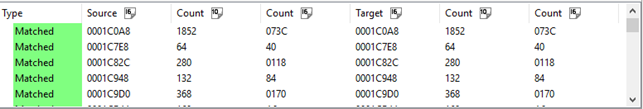
Binary comparision result:
Credits: DiDA and Caoyin
CPAntiDumper created by Caoyin is a tool that obfuscate binary files and .dylibs and prevent others from dumping offsets. It support ARMv7 and ARM64 iOS Binary and Android ARM binaries. ARM THUMB and x86 are currently not supported yet.
Note: CPAntiDumper will not prevent IDA Pro from disassembling
Download:
For ease of use, DiDA have included a CPAD.bat file inside the download link below which simplifies the whole process by simply dragging your binary file to the .bat file and reading the on-screen instructions. Of course, you can modify the .bat to your liking. You will also need to edit it to add the location of cpad.exe on your computer. Example usage of CPAD.bat file.
NOTE CPAD is only a Windows tool but will likely work on other operating systems with Wine since it's a simple CLI.
If you would like to run CPAD using cmd, you can do so using this command:
cpad.exe BINARYFILENAME VALUE ARCH
iOS Examples:
Code:
cpad.exe baba 15000 arm64
cpad.exe iosfps 25000 armv7Android Example:
Code:
cpad.exe libmarvel.so 2000 elfarmv7Once you run the command, CPAD will analyze the binary and start obfuscating it thus preventing Binary Compare.
Once CPAD completes the process, it will generate 2 new files. BINARYNAME(.so)obf & BINARYNAME.txt
BINARYNAME(.so)obf will be the obfuscated binary file you will need to use. Rename the file and place it back into your IPA/APK and test/share your hack.
BINARYNAME(.so).txt will be the file that contains all the writeData instructions for you to implement inside your Tweak.xm. Most effective way to integrate all the writeDatas inside the .txt to your Tweak.xm is by placing your real writeData in a random place amongst all the other CPAD writeDatas. So if someone tries to dump your offsets, they will have to go through <YOURVALUE> (20,000 other writeDatas for example). This is only for iOS .deb hacks.
Example:
Code:
vm_writeData(0x100673DC0,0xC0033FD6); // writeData Generated by CPAD
vm_writeData(0x100A969D8,0x2100014A); // writeData Generated by CPAD
vm_writeData(0x100A969DC,0x420002CB); // writeData Generated by CPAD
vm_writeData(0x100A969E4,0x210001CB); // writeData Generated by CPAD
vm_writeData(0x10051EBF8,0xE00300AA); // writeData Generated by CPAD
vm_writeData(0x100114DF8,0x12345678); // Your Real Offset!
vm_writeData(0x10051EC44,0x000000CB); // writeData Generated by CPAD
vm_writeData(0x10051EC4C,0x840004CB); // writeData Generated by CPAD
vm_writeData(0x10051EC6C,0xC0033FD6); // writeData Generated by CPAD
vm_writeData(0x10051EC74,0xE20302AA); // writeData Generated by CPAD
vm_writeData(0x10051EC88,0xE10301AA); // writeData Generated by CPADRemember! You can go crazy with your value by entering 100000 into CPAD which will make it super secure but will likely take a lot of time depending on your computer.
NOTE: For CPAD to be more efficient. Use it AFTER you have modded your binary.
Binary comparision result:
Credits: DiDA and Caoyin
Last edited: